Phishing PDF Document Story
Background
A few days ago, we detected a PDF file with a non-zero detection score on VirusTotal, however, almost all the detections have only a kind of “generic” results. Moreover, further investigation revealed that the same file was two weeks ago without any detections on VirusTotal. We continued with a deeper analysis of this document and its behavior to determine if this is only a false-positive alert, or if it can be a serious problem for those, who already opened this PDF document.
Note: this article was originally published on LIFARS blog; I posted it here only as a reference of my work
Static analysis of PDF document
The captured sample is a PDF document with the filename “Employee Satisfaction Survey..pdf”.
First, let’s look at VirusTotal detections.
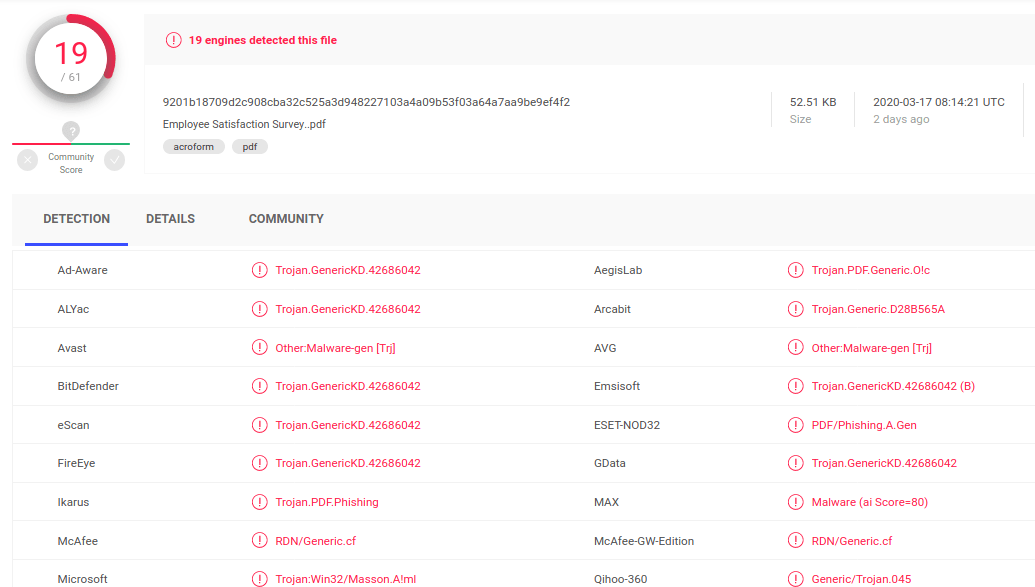
As we can see, the PDF file is detected as malicious with 19 of 61 antiviruses, but almost all of them report it only as a “generic trojan”. There are two mentions of “phishing” and only one non-generic keyword can be found: Masson (as detected by Microsoft Defender). However, the description of this Masson threat by Microsoft is not very useful, it contains the following generic statement only:
“This threat can perform a number of actions of a malicious hacker’s choice on your PC.”
So, why are many of the antiviruses detecting this file as malicious if they do not provide us with something more specific about this threat instead of several generic keywords? Can the sample be innocent, and these generic detections are caused by some false-positive artifact (picture, string, a sequence of bytes) inside this PDF? Or is it really dangerous? And if yes what happens to the victim who opened it? Can be their network compromised?
To answer these questions, we need to look deeper into the document. Let’s continue with a manual static analysis. We can examine the structure of the PDF document and search for artifacts most often used for malicious purposes like JavaScript execution, automatic actions on opening the document, etc.
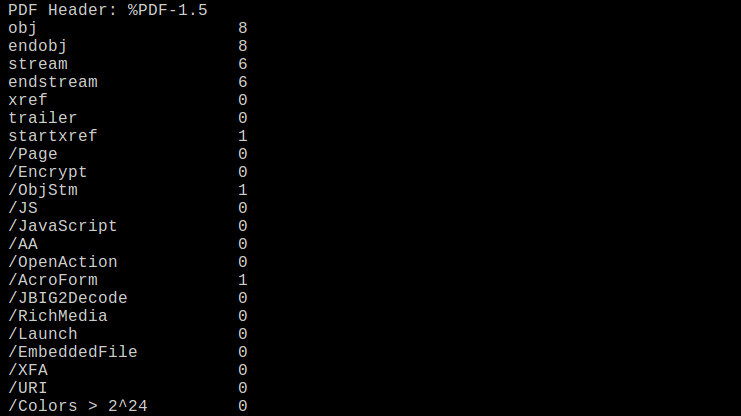
The triage reveals that this PDF sample doesn’t contain any embedded JavaScript, no automatic OpenAction, and no command execution (Launch), but it contains one AcroForm – this can be potentially dangerous. So, we can continue with parsing the PDF document structure and we will look at suspicious artifacts carefully.
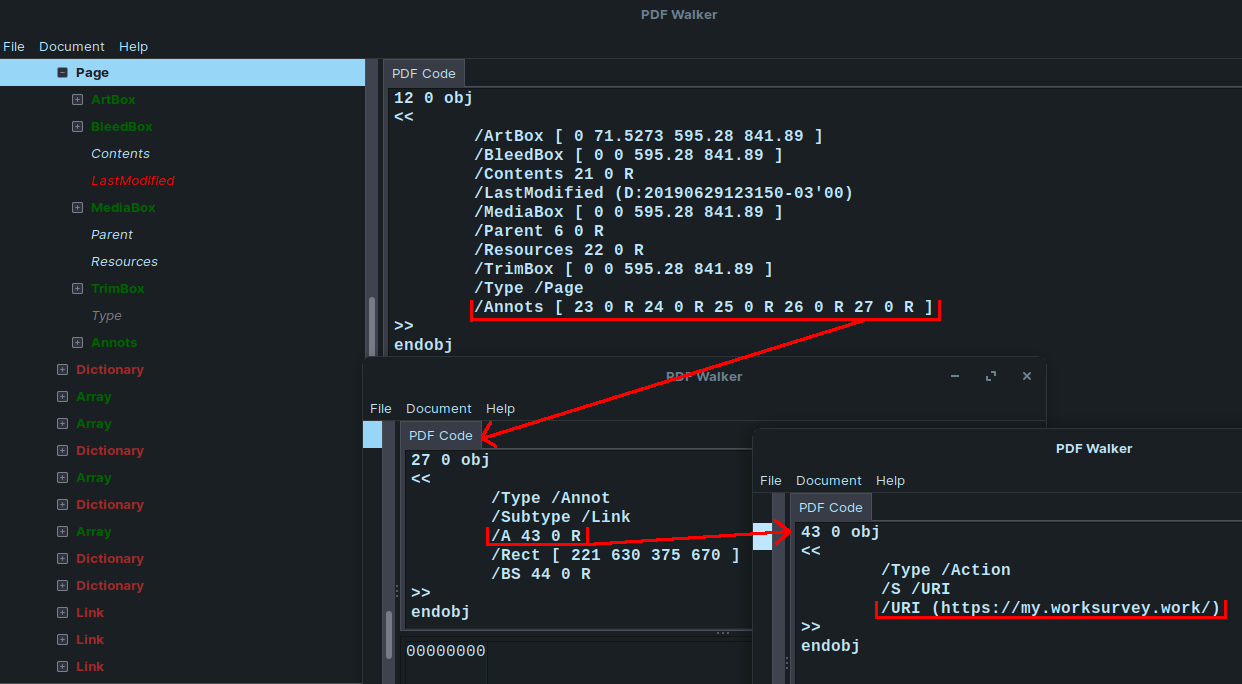
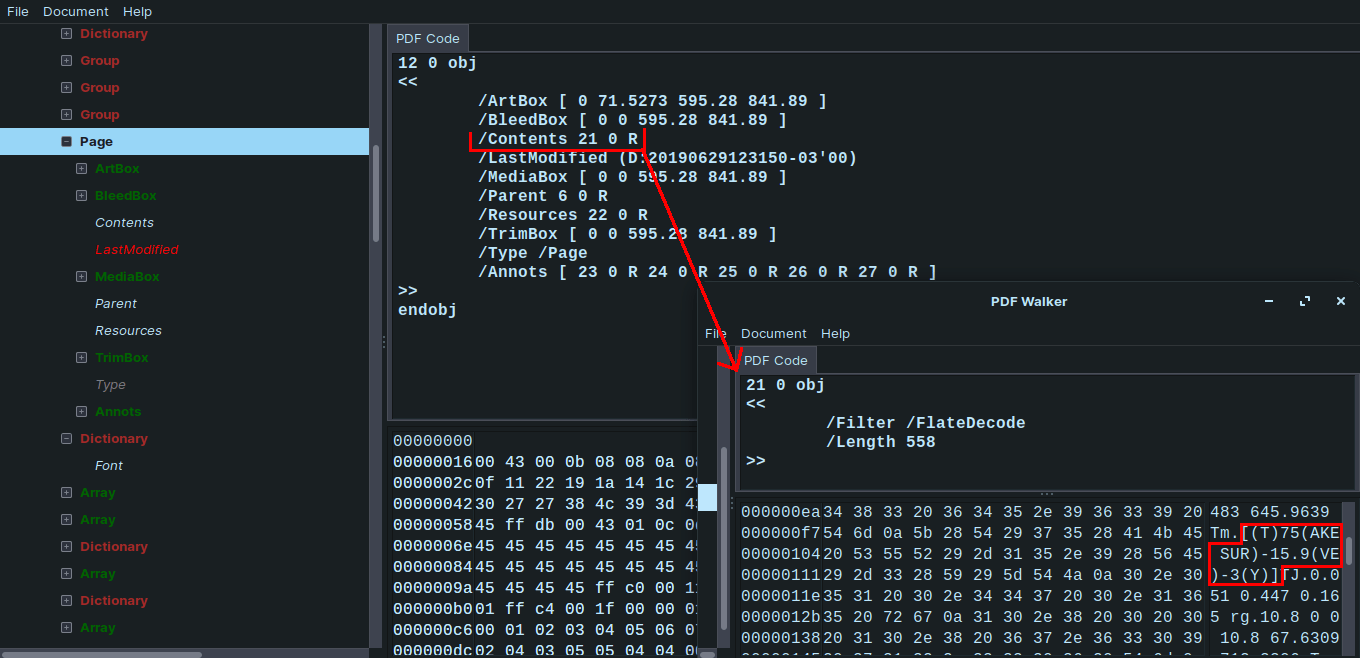
Inspection of the PDF sample shows us that this PDF document contains only one page with an image, but with 5 annotations, too. The detailed inspection reveals that these annotations are almost in the same place and all of them are associated with the actions of type URL for resolving the Uniform Resource Identifier, which causes the resolving and opening of the desired URL (typically the destination of hypertext link) when user click on it. In this case, we found the following 5 URLs:
- hxxps://pr46grb084surv.appspot.com/
- hxxps://mwz31548ryn19.appspot.com/
- hxxps://example.com
- hxxps://surveyportal.work/MySurvey/
- hxxps://my.worksurvey.work/
We will cover these URLs later, but for now, we can focus on the abovementioned content of the one-page: image. It is a screenshot of some survey and it is blurred – probably it will be part of the social engineering trick known from the Microsoft Office malicious documents such as “In order to view the protected content, click on Enable/Allow button”.

When we look back to the Page and its Contents, we find inside this object the text “TAKE SURVEY”. So, this could be another part of social engineering trick that caused the user to click on the annotation.
Now, let’s look at the extracted URLs. Besides the innocent one (example.com), the four others look suspicious. However, the first three are not working anymore during our analysis, only the last one contains something: phishing website related to “this mandatory and confidential survey”.
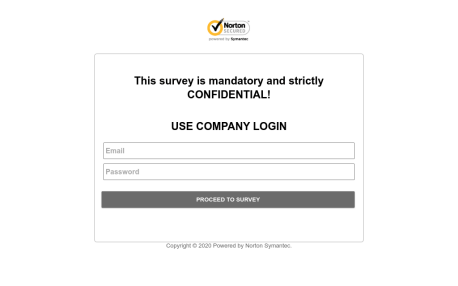
Somebody may ask the question of why there are 5 annotations when the only one contains phishing stuff. One of the answers can be for example, that the rest 4 Annotations are only remnants from creating and testing this PDF document by attackers.
Behavioral analysis of PDF document
Now we know pretty much about this document. Just for completeness of this analysis we can proceed with behavioral analysis and verify our findings from static analysis. We executed this document in a sandbox. There are a couple of online tools available to do that, but because we need to simulate user click, we need to use an interactive sandbox – e.g. Any.Run or some Virtual Machine.
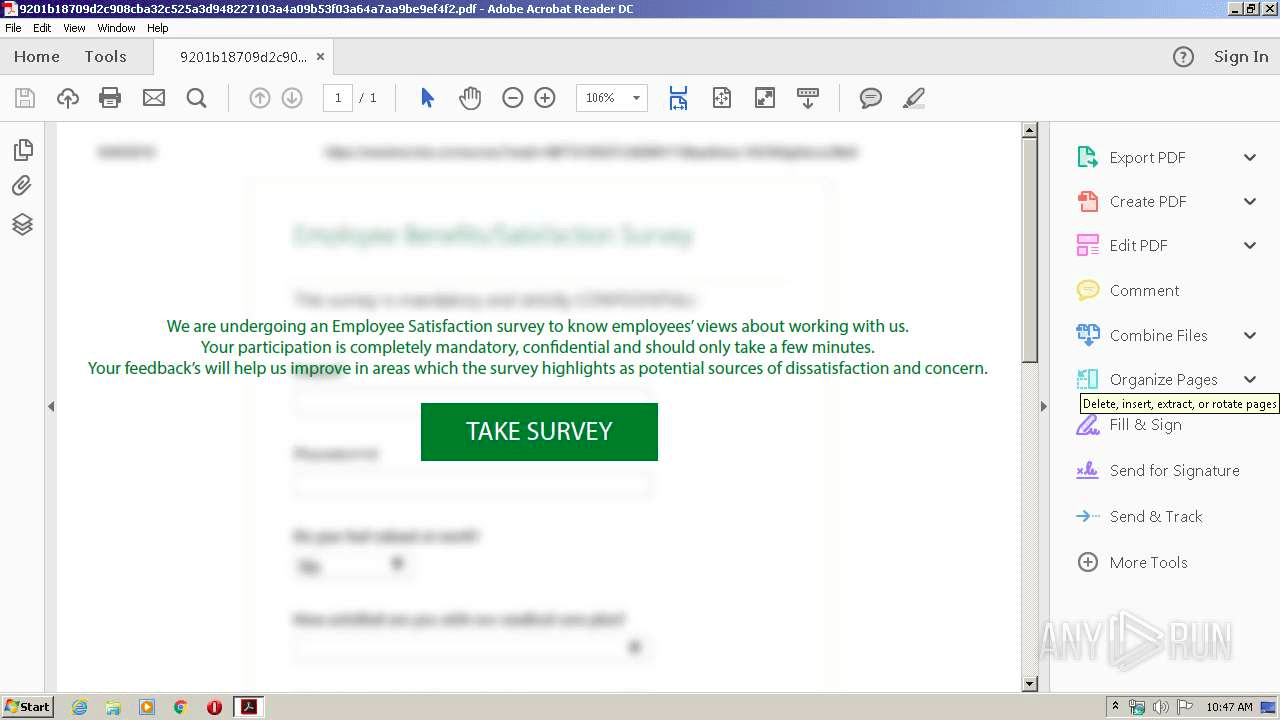
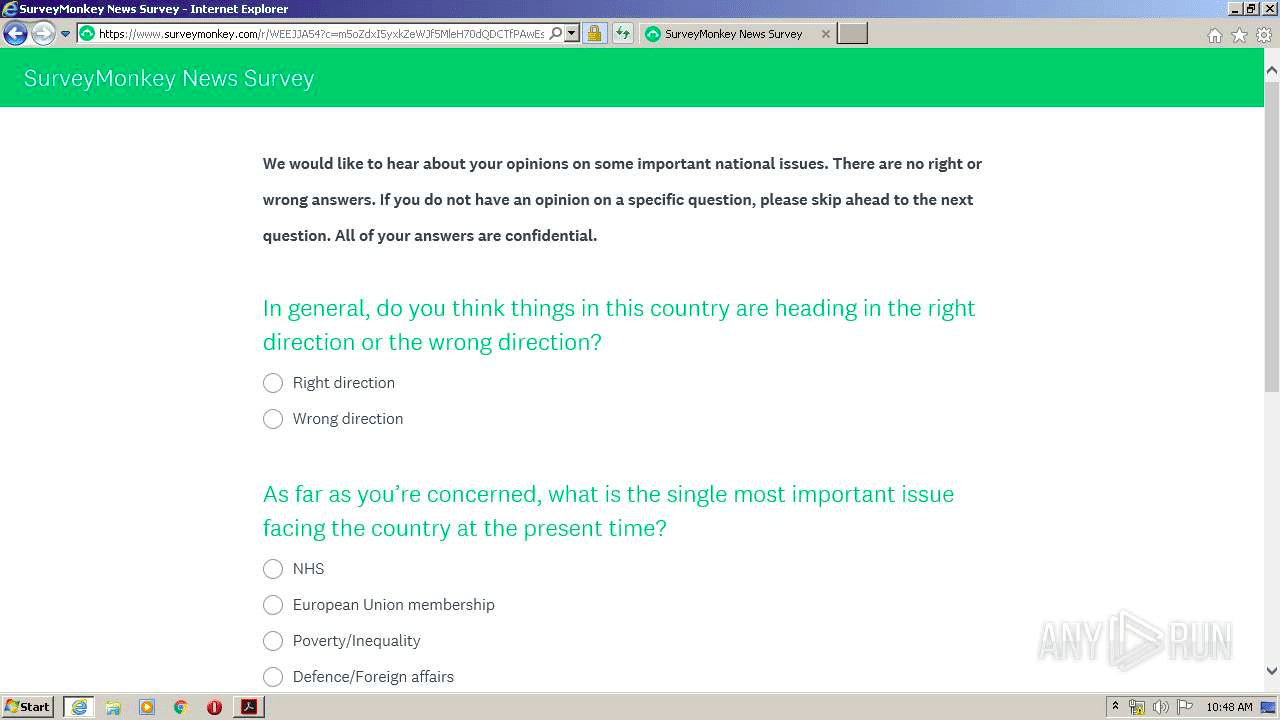
When we opened this PDF document on Any.Run, we can see that we were correct – blurred image of the survey as a background and big green button TAKE SURVEY – this is social engineering technique.
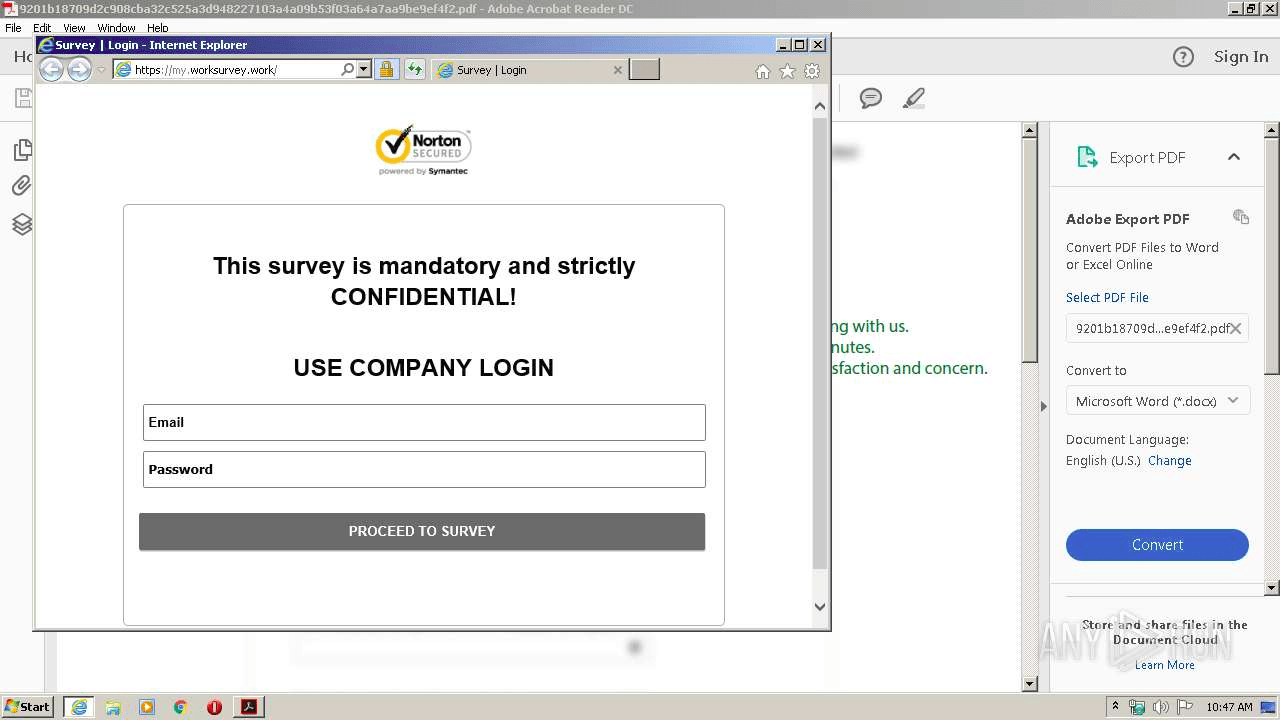
After we clicked on the TAKE SURVEY button, the URL with the phishing site was opened in the web browser. It asked us for fill company email and password.
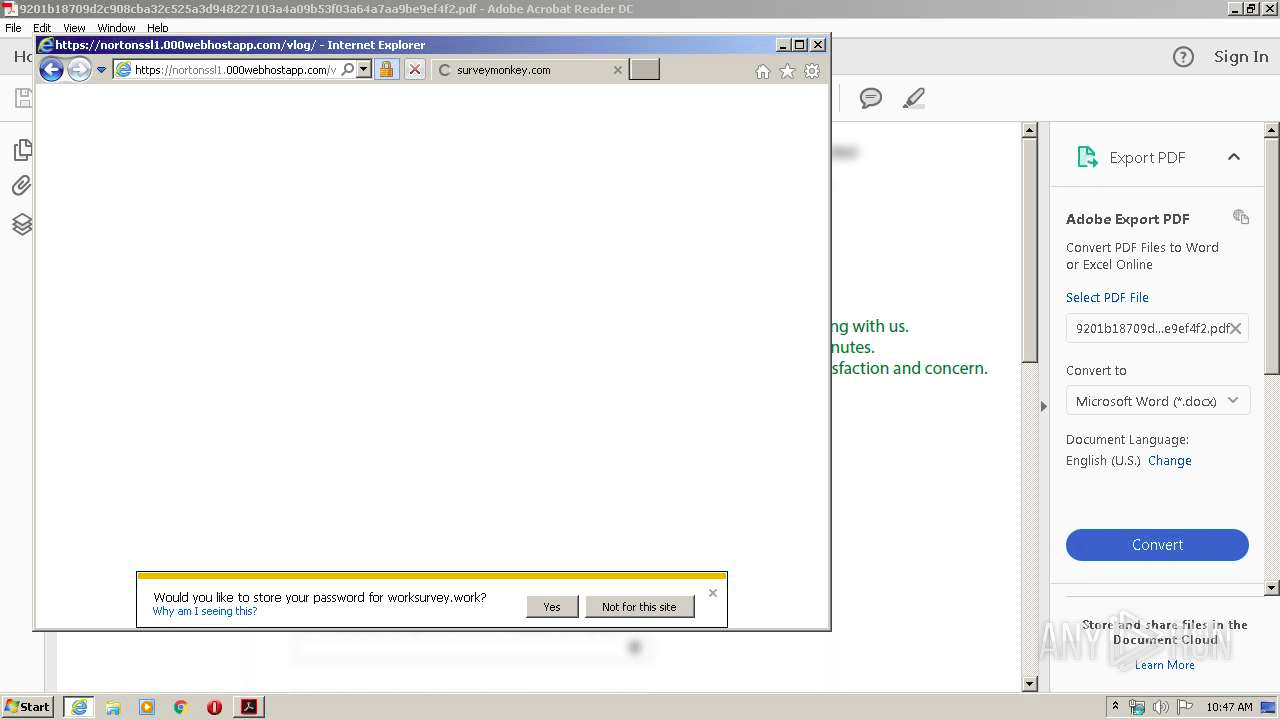
After filling in some values and submitting them, this website sends us to another suspicious domain “nortonssl1.000webhostapp.com”, which redirects us to the SurveyMonkey website with a legitimate survey.
Summary
After we analyzed the suspicious PDF document, we conclude that this document is part of a phishing campaign that asks users to provide their company credentials on the phishing website. However, this document itself doesn’t contain the execution of malicious code, so only opening of the document (without any interaction) doesn’t compromise the victim device.
Using provided Indicators of Compromise (IOC) below it can be verified if any of recipients of this PDF document performed any action like clicking on the TAKE SURVEY button and they visited the phishing website or submitted any data to the attackers.
Indicators of Compromise (IOC)
- Sample Details
- FileName: Employee Satisfaction Survey..pdf
- FileSize: 52.51 KB (53774 bytes)
- MD5: 0db95d236def05003f44bc7ca3cf0fee
- SHA1: b5eb9f6a2afd6a4050c532bf05d040e9ff82aa4e
- SHA256: 9201b18709d2c908cba32c525a3d948227103a4a09b53f03a64a7aa9be9ef4f2
- Network Domains
- pr46grb084surv.appspot.com
- mwz31548ryn19.appspot.com
- surveyportal.work
- my.worksurvey.work
- nortonssl1.000webhostapp.com
- Network IPs
- 198.54.126.77
- 145.14.144.161