“Hidden” Bundpil
Introduction
My friend have got one USB stick infected with malware, at least that’s what one AntiVirus product reported about it. But strange thing happen, it seemed that the detected file was not present on this USB key. Not only the detected file, but also all of the user data was missing. Only one .lnk file was present in the root of the filesystem. So, this is point where our investigation begins…
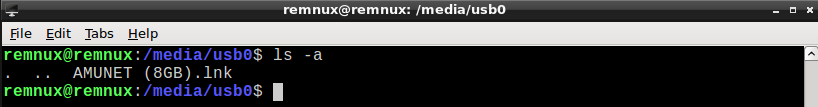
Analysis
If we look into the AMUNET (8GB).lnk file, we can see that it runs the file from this USB stick. (Actually, it starts the rundll.32.exe via the cmd.exe).
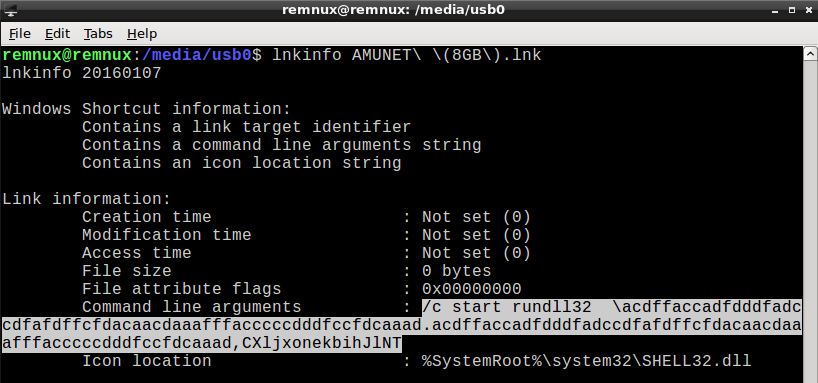
But the question is, where is this file with this extra long name hidden? And the answer is: it is placed in the hidden directory with nonprintable name (”\xC2\xA0”), as we can see in the next picture (there are also all of the missing user data).
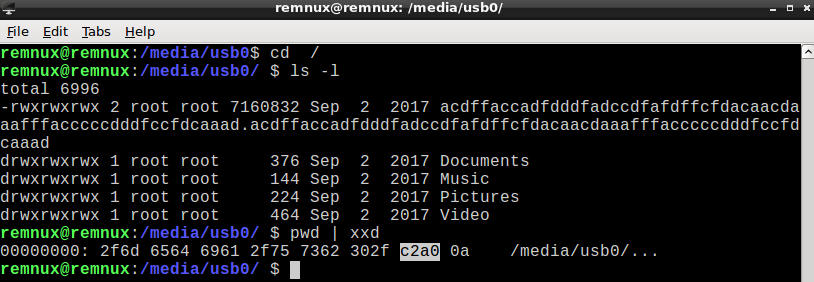
The nonprintable directory name is the reason, why some tools have problems with displaying it, and/or don’t work with its filepath correctly. As we can see from the output of file or exiftool, the sample is Win32 DLL with filesize aprox 6.9MB. It is detected as malicious by 44 antiviruses on VirusTotal, in most cases as a variant of Zusy or Bundpil, see output from vtTool.py:
$ vtTool.py -hash 560c5609bdad5e2a30cbd2a48df2a711
██╗ ██╗████████╗████████╗ ██████╗ ██████╗ ██╗
██║ ██║╚══██╔══╝╚══██╔══╝██╔═══██╗██╔═══██╗██║
██║ ██║ ██║█████╗██║ ██║ ██║██║ ██║██║
╚██╗ ██╔╝ ██║╚════╝██║ ██║ ██║██║ ██║██║
╚████╔╝ ██║ ██║ ╚██████╔╝╚██████╔╝███████╗
╚═══╝ ╚═╝ ╚═╝ ╚═════╝ ╚═════╝ ╚══════╝ v0.9.3
Find the name of the evil
Robby Zeitfuchs, Mark Lawrenz
Copyright (c) 2013-2015
--- scanner malware classification ---
ransomware: 1
dropper: 0
exploit: 0
downloader: 0
riskware: 0
rootkit: 0
worm: 4
trojan: 16
--- average detection rate ---
count hashes: 1
totalscanner: 71
positives: 44
--- scanner malware family determination ---
Most frequent word: zusy (count=8)
Second most frequent word: bundpil (count=7)
Also the Intezer identifies this sample as Tinba (another name for Zusy malware). Intezer is platform for analyzing the code reuse between the malware families, in many cases it can be very useful for identification of the unknown samples. As Intezer says about itself:
Intezer Analyze™ dissects binary code into thousands of small code fragments (genes), then compares them to a massive database that contains genes from malware and legitimate software, effectively providing a full DNA mapping of each executable.
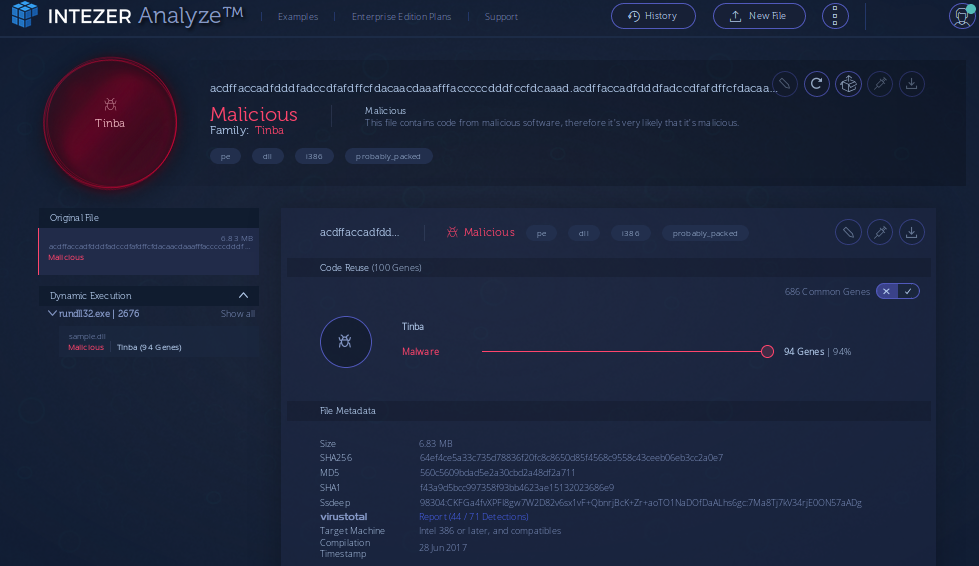
Unfortunatelly, in this case it turns out that our sample is not the variant of Zusy or Tinba (Tiny banker trojan), which is usually much smaller then 6.9 MB. The second most frequent detection as a worm called bundpil seems more legit. Moreover, also the description from the ESET mentions the .lnk files with the names exactly like in this case:
The worm creates the following files:
%removabledrive%\%drivename% (%drivesize%GB).lnk %removabledrive%\My Removable Device.lnk
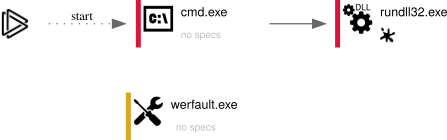
Next step is to proceed with behavioral analysis. We can try to run our sample at Any.Run interactive sandbox using the command extracted from .lnk file before (cmd.exe and rundll32.exe):
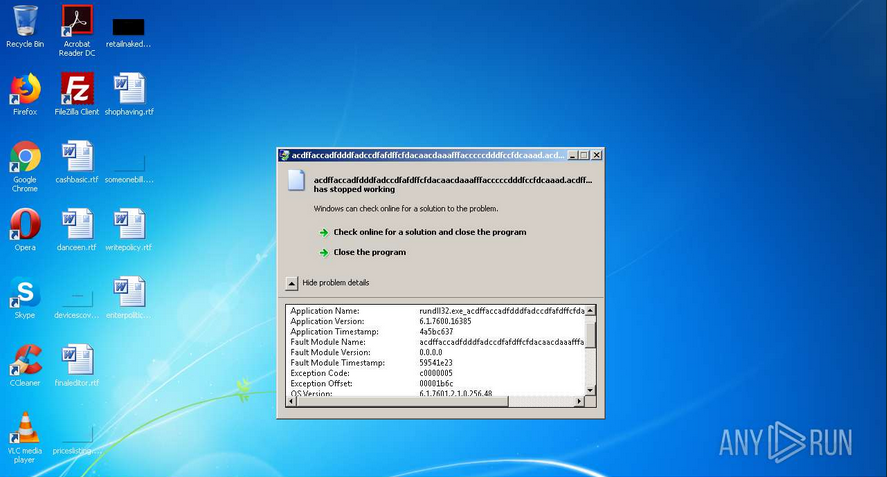
This execution leads to the application crash, with exception at offset 0x00001b6c in our sample:
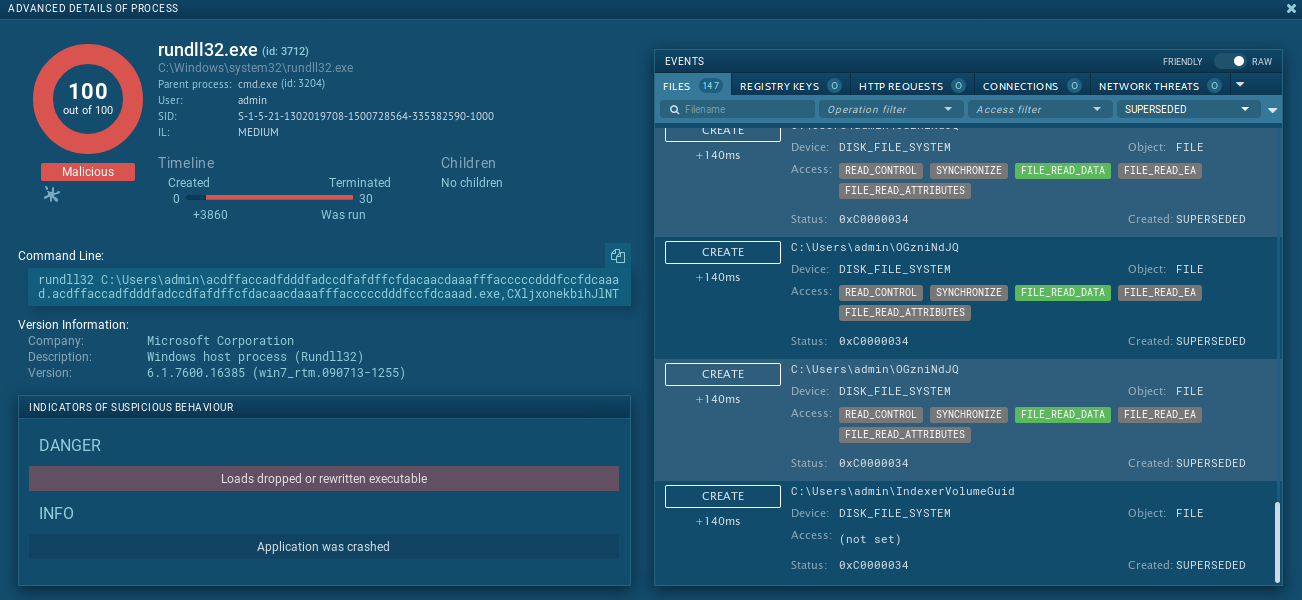
Hovewer, the analysed sample tries to access (open, read) some files, mostly with random-look names, like:
bidyqxlmgedskivduSseXbSXAidDp.DLLV9onexQlw0aJf9zqEQocSXNVrjXnaMCzbYuvnAjOGzniNdJQIndexerVolumeGuid
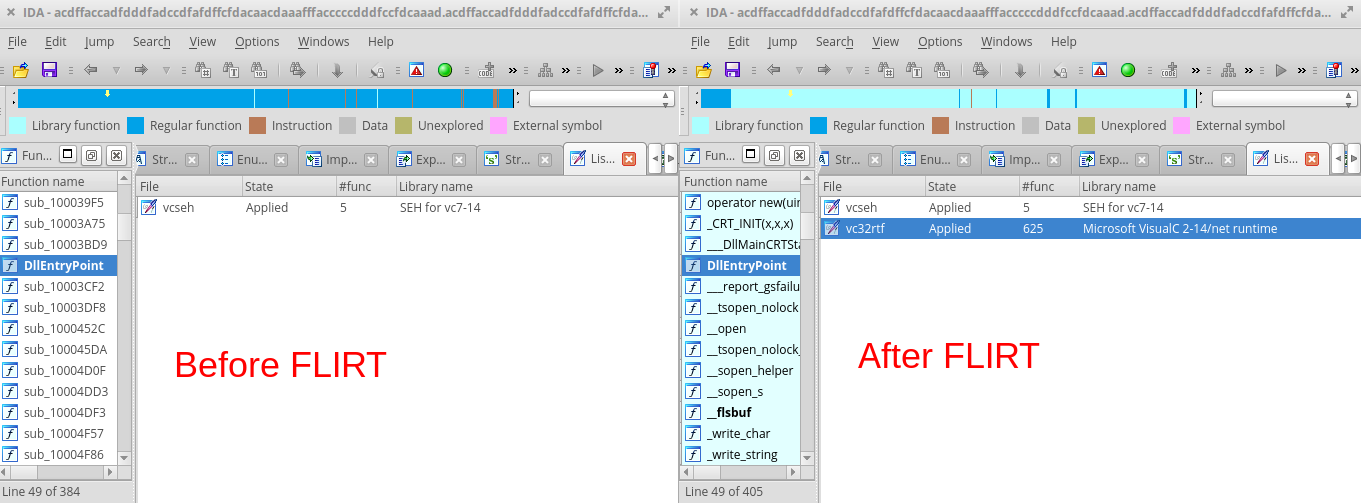
Now, we will get more info about intended behavior using Ida disassembler. We can look at the exception offset and also we can try to find references to the filenames listed above. One tip for Ida: after loading the sample don’t forget to use FLIRT signatures, in this case it identifies more then 600 library functions (because static linking of C Runtime library) and only small portion of the code still remain to analyze:
Sample tries to load the first file as library in new thread, so if this file exists somewhere in DLL search path, it will be loaded and its DllEntryPoint will be executed.
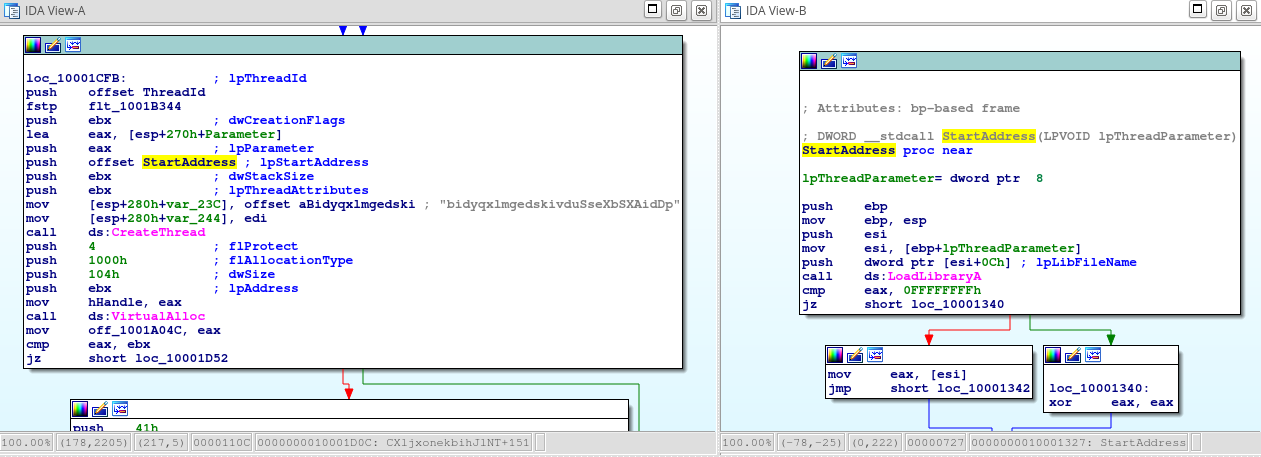
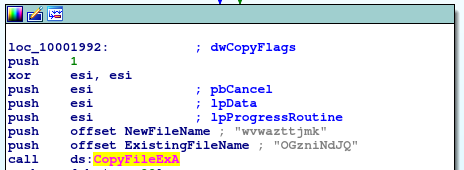
There are also a lot of junk code, for example the third filename in the list above is just for the obfucsation. If this file exists, its copy will be created with another messy filename:
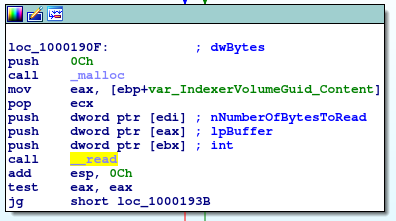
On the other hand, the last one file, IndexerVolumeGuid, is interesting. Again, scattered between lot of junk code, there are constructing the filepath %malwaredir%\IndexerVolumeGuid, reading its content:
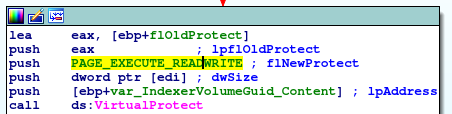
changing permissions of memory page to Read-Write-Execute:
decrypting it (by the way, this is the code where application crash was occured during the execution at Any.Run, because no IndexerVolumeGuid was present and the sample tried to decrypt uninitialized memory from the heap):
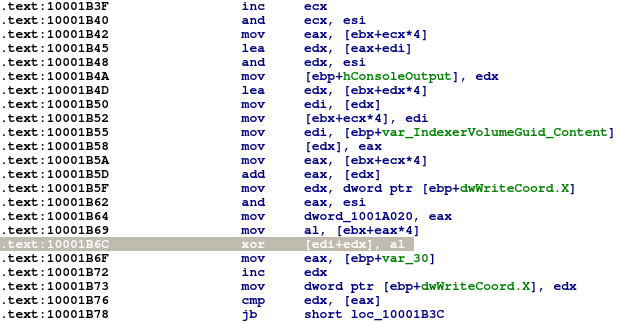
and finally, call the decrypted code:

Conclusion
The analysed sample was the worm Bundpil, which is able to spread via removable media. It can hide files inside the directory with nonprintable name and using the .lnk file in the root of the removable media it starts the hidden DLL loader of main payload, which is placed as the file IndexerVolumeGuid in the hidden directory, too.
Note
Unfortunatelly, in my case, I did not make a full copy (or binary image) of the infected USB stick, because lack of time, I only made a copy of the .lnk file and DLL loader, which I found after very quick analysis. So, this is the reason, why I did not present also detailed analysis of the decrypted content of the IndexerVolumeGuid.
Samples
| File name: | acdffaccadfdddfadccdfafdffcfdacaacdaaafff acccccdddfccfdcaaad.acdffaccadfdddfadcc dfafdffcfdacaacdaaafffacccccdddfccfdcaaad |
| File size: | 7160832 B |
| File type: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | 560c5609bdad5e2a30cbd2a48df2a711 |
| SHA1: | f43a9d5bcc997358f93bb4623ae15132 023686e9 |
| SHA256: | 64ef4ce5a33c735d78836f20fc8c8650 d85f4568c9558c43ceeb06eb3cc2a0e7 |
| SSDeep: | 98304:CKFGa4fvXPFI8gw7W2D82v6sx1 vF+QbnrjBcK+Zr+aoTO1NaDOfDaALhs6 gc:7Ma8Tj7kV34rjE0ON57aADg |
| Sample origin: | Infected USB Stick |
| Capture date: | 28.12.2018 |
| Date of analysis: | 14.02.2019 |
| Analysis type: | Quick Analysis |
| Affected systems: | OS Windows XP and newer |
| AV detection | 44⁄71 VirusTotal, timestamp: 2018-12-28 22:44:03 |
| ESET NOD32 | Win32/Bundpil.EG |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| Microsoft | |
| Symantec | SMG.Heur!gen |
| Tags: | Bundpil, Worm, LNK |
| Exiftool | |
| FileType | Win32 DLL |
| FileTypeExtension | dll |
| MIMEType | application/octet-stream |
| MachineType | Intel 386 or later, and compatibles |
| TimeStamp | 2017:06:28 23:22:43+02:00 |
| PEType | PE32 |
| LinkerVersion | 10.0 |
| CodeSize | 74752 |
| InitializedDataSize | 37888 |
| UninitializedDataSize | 0 |
| EntryPoint | 0x3ccf |
| OSVersion | 5.1 |
| ImageVersion | 0.0 |
| SubsystemVersion | 5.1 |
| Subsystem | Windows GUI |